In this edition of the Road Map to PCI, we move to the final requirement – Develop and maintain secure systems and applications. This requirement must be met in order to successfully Maintain a Vulnerability Management Program. This is the 6th of 12 PCI DSS requirements and also brings us to the conclusion of the 3 out of 6 areas of focus that the PCI Council has created.
The PCI Council requires that any merchants who belong in either Self Assessment Questionnaire C, C-VT, or D must address requirement 6. For the purposes of this blog, we will look at Requirement 6 through the lens of Self Assessment Questionnaire C and C-VT.
Ensuring that you develop and maintain secure systems and applications is critical in ensuring the security of cardholder data when transactions flow through your processing methods. It is also very important to remember that this requirement applies to ALL systems and applications within your card data environment that the network card data transmits through.
Addressing Security Vulnerabilities
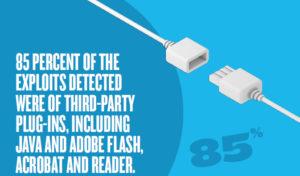
Photo courtesy of Trustwave 2014 Global Security Report
The importance of this requirement is significant because users with malicious intent are constantly discovering and exploiting new vulnerabilities in systems and applications.
The Trustwave Global Security Report for 2014 was recently released and noted that over the course of 2013, roughly 85% of exploits originated from plug-ins such as Adobe Flash, Java and Acrobat Reader. These exploits enable the bad guys to do a variety of things, such as monitor your network to see what data you access, or track what types of data to steal such as passwords, phone numbers, card numbers or other sensitive information.
Luckily, many of these companies are quick to post new patches and security updates, sometimes even multiple times in the same day. However, these firms can only do so much when addressing vulnerabilities. Posting patches is generally the most they can do from their end. At the end of the day, it is the device user or appointed IT staff’s responsibility to make sure that these patches are installed in a timely manner. It is important to know that patching vulnerabilities within 30 days is required by the PCI DSS.
Zero Day Vulnerabilities
The hackers behind Zero Day Vulnerabilities are the reason that more often than not, your workstation wants to update something when you power it up in the morning. Zero Day Vulnerabilities have been in the wild for some time now, running completely undetected and making them especially nasty. According to many reports, these can be very profitable, often netting 6 figures for those who find them if the exploit sells on the black market.
Speed to Implementation is Key
Installing the newest patches and security updates as quickly as they are available is very important to take care of on your own systems; you will always want to be sure your service providers are on top of this as well. Current reports, such as this report from Fox Business, indicates that approximately 50% of the servers worldwide that were affected by the Heartbleed vulnerability are still susceptible to this bug more than two months after its discovery.
Meeting the Requirement
Ensuring that all systems and applications on your network are updated as soon as possible (within 30 days of the patch release), will keep you in line with requirement 6 to Develop and Maintain Secure Systems and Applications. Appointing a particular member of your team to oversee this patching will simplify the process and help keep you secure.
You will also want to make sure that users on your network do not have access rights to install applications that may go unnoticed. The safest way to take care of this is to make sure that an administrator login/password is required in order to install new applications or make system changes.
Putting these items in place should keep you in compliance with the PCI DSS Requirement 6, however if there is any doubt, be sure to reach out to your Merchant Services Provider or Qualified Security Assessor to confirm if there is anything further that can be done.
Join us again in July when we look forward to requirements 7, 8 and 9 of the PCI DSS which compose the fourth area of focus, Implement Strong Access Control Measures.
If you have any questions about PCI that you would like to see covered, let us know! You can email us at compliance@cashlinq.com to share your thoughts or questions which we may then address here on our blog!